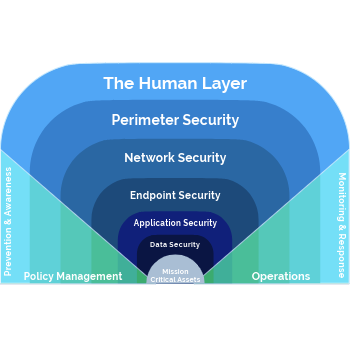
Assured Digital Technologies (ADT) provides comprehensive multi-layered security solutions that protect your entire digital infrastructure. From perimeter defences to mission-critical assets, we ensure your business is secure and compliant in an evolving threat landscape.
Our approach starts with the Human Layer, offering security awareness training and access control policies to reduce human error and restrict sensitive data access. This is reinforced by Perimeter, Network, Endpoint, and Application Security, deploying advanced encryption, threat detection, and monitoring tools to safeguard your systems and data.
At the core, we protect your mission-critical assets with tailored security measures. With 24/7 monitoring, rapid response capabilities, and a focus on ISO 27001, ISO 9001, and Cyber Essentials compliance, ADT delivers robust, scalable protection across all layers of your organisation.