As Head of Technology at Assured Digital Technologies, I have seen how rapidly the cyber threat landscape changes. With over 30 years in the IT industry, I have witnessed everything from minor breaches to attacks that have significantly impacted business operations and revenue. Today, I want to discuss Defence in Depth cybersecurity. This strategy uses multiple layers to protect information assets. In 2024, it is more important than ever.
Understanding the Cyber Threat Landscape
Cyber threats are becoming more complex and frequent. The Cyber Security Breaches Survey 2024 found that 59% of medium-sized businesses and 69% of large businesses in the UK had a cybersecurity breach in the past year. Additionally, 31% of businesses experienced breaches weekly [1]. The National Cyber Security Centre (NCSC) also warns of “enduring and significant threats.” These threats come from state-sponsored cyber actors and organised crime groups. They often target the UK’s critical infrastructure [2]. With cybercrime costing the UK economy £17 billion annually [3], a Defence in Depth cybersecurity approach is crucial.
What is Defence in Depth?
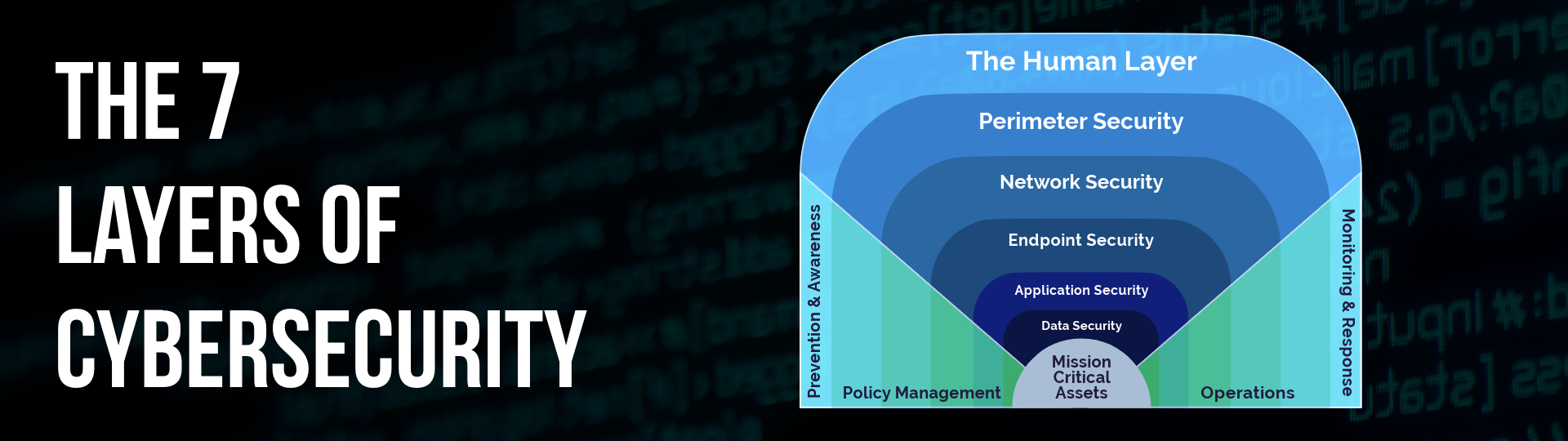
Defence in Depth is a multi-layered cybersecurity strategy. It is designed to protect an organisation’s data, systems, and networks. No single security measure is perfect. Therefore, using multiple layers—such as data security, application security, endpoint security, and network security can significantly improve an organisations cybersecurity posture.
Key Components of Defence in Depth Cybersecurity
Here are the essential layers that make up a robust Defence in Depth strategy:
- Data Security Controls: Policies, procedures, and access controls to protect sensitive data from unauthorised access and breaches. Regular data audits and encryption can also enhance data security.
- Application Security Controls: This involves using multi-factor authentication (MFA), authorisation protocols, and secure coding practices to minimise vulnerabilities. Regular vulnerability assessments and patch management are also crucial.
- Endpoint Security: Solutions like antivirus, Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR) help detect and neutralise threats at the endpoint level, which is often the first target in an attack.
- Network Security: Utilising firewalls, Virtual Private Networks (VPNs), intrusion detection systems, and Data Loss Prevention (DLP) tools to protect the network’s integrity and prevent unauthorised access.
- Perimeter and Physical Security: Ensuring robust access controls and securing physical data centres and devices. This is particularly important in preventing insider threats and unauthorised physical access.
- Human Layer: Often overlooked, the human layer is one of the most critical. Regular cybersecurity awareness training, simulated phishing attacks, and behaviour analytics are essential to build a culture of security within the organisation.
Real-World Evidence: A Multi-Stage Cyber Attack on a UK Manufacturer
To highlight the importance of a multi-layered approach, I referenced a recent case during my presentation. In 2021, a leading UK-based manufacturer, with operations in 25 countries, faced a major ransomware attack. This company had layers like backup solutions, disaster recovery (DR) infrastructure, and antivirus protection. Yet, the attackers exploited various vulnerabilities over several months. This real-world example shows how critical a Defence in Depth cybersecurity approach is.
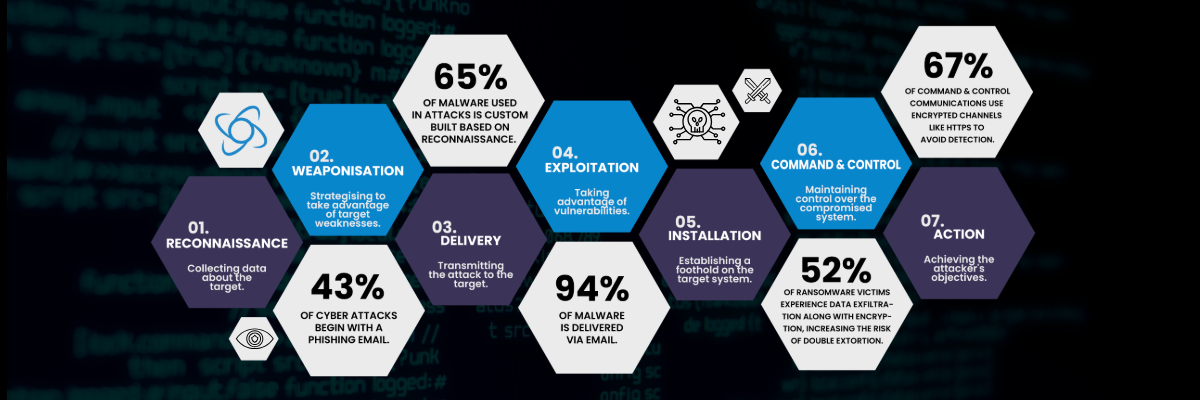
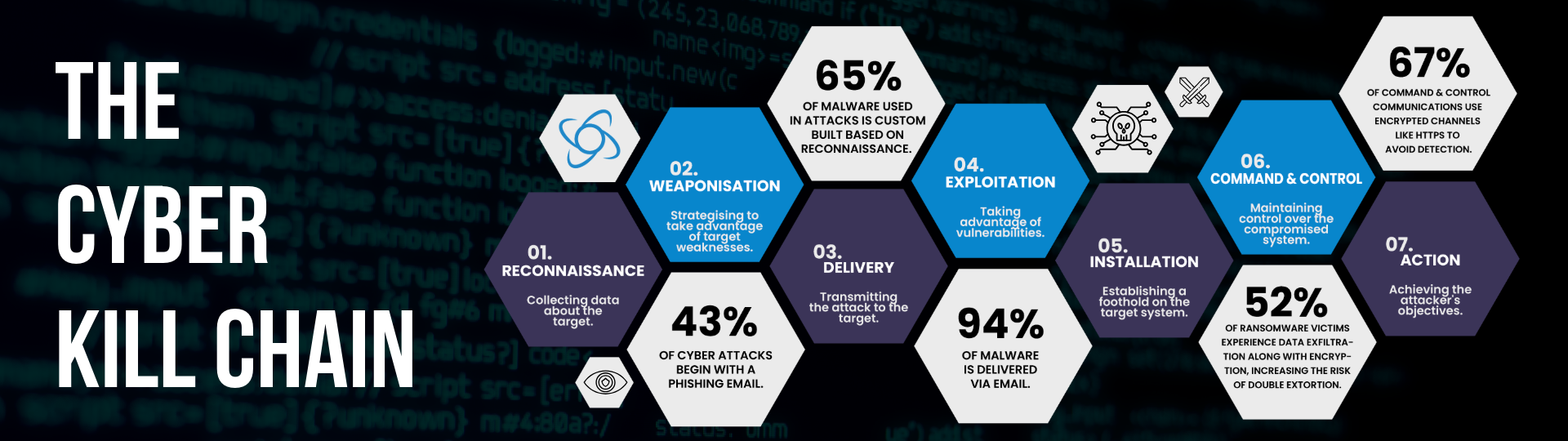
The attack followed the seven stages of the Cyber Kill Chain:
- Reconnaissance: The breach began with a phishing email sent to a user in the production facilities in Southeast Asia. Once a foothold was established, the attacker’s obtained information about applications, operating systems and infrastructure.
- Weaponisation: The attackers created a strategy to further exploit the breach, developing attack vectors to elevate privileges, moving laterally across the network to gain access to business-critical systems.
- Delivery: Several sophisticated tools such as Mimikatz, were deployed to the target network to identify and exploit vulnerabilities, gain administrative control and initiate additional points of entry.
- Exploitation: Following delivery, the attackers exploited vulnerabilities within the network to escalate privileges and establish control. They gained higher-level access to critical systems, applications and data.
- Installation: The attackers installed malware and other tools to compromise cyber defences, attack BCDR systems, exfiltrate data and encrypt data and applications.
- Command and Control: Establishing a command and control presence, the attackers coordinated their activities across multiple sites, including locations in Southeast Asia, the US, Europe, and the UK.
- Actions on Objectives: Finally, the attackers exfiltrated sensitive data and compromised backup and recovery systems. Then disabled malware protection and encrypted data and applications across the organisation. The ransom demand for recovery was £750,000.
The impact was severe—global manufacturing stopped for over two weeks, business operations were disrupted for six weeks, data was stolen and published online, and the company faced significant reputational and financial damage. This example starkly illustrates the need for a comprehensive Defence in Depth cybersecurity strategy.
Key Takeaways for Organisations
Based on this example and my experiences, here are key strategies that every organisation should consider as part of a Defence in Depth cybersecurity approach:
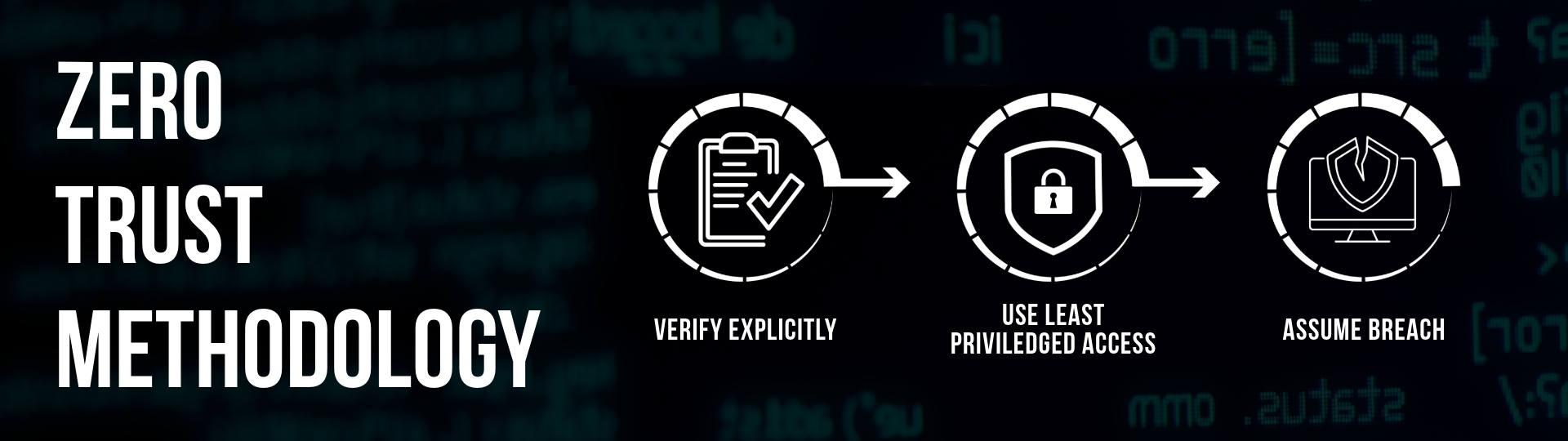
- Zero Trust Principles: Implement a “never trust, always verify” model. Ensure that every access request is authenticated and authorised, and grant minimal access necessary for specific roles.
- Immutable Backups and Air-Gapped Systems: Ensure backups cannot be altered and are stored in isolated systems to prevent tampering. This is critical for data integrity and business continuity.
- Advanced Endpoint and Network Protection: Deploy tools like XDR and maintain continuous network monitoring to detect unusual activities and respond to threats swiftly.
- Regular Training and Simulated Attacks: Conduct regular phishing simulations and provide cybersecurity training to reduce the likelihood of successful social engineering attacks.
- Comprehensive Incident Response Planning: Have a well-documented incident response plan and work with cyber insurance providers to manage both financial and operational impacts in case of a breach.
Conclusion
No single security solution can provide absolute protection. However, by implementing a comprehensive Defence in Depth cybersecurity strategy that integrates multiple layers of protection – spanning technology, processes, and people—we can significantly reduce the risk of a successful attack and ensure our organisations are better prepared to recover swiftly from incidents.
If you’d like to discuss how we can help you build a multi-layered defence strategy tailored to your organisation’s needs, don’t hesitate to contact us at Assured Digital Technologies for a free consultation. Let’s work together to fortify your cyber defences and protect what matters most.
Sources
- Cyber Security Breaches Survey 2024, GOV.UK, available at: https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2024.
- National Cyber Security Centre (NCSC), “Enduring Significant Threat to UK’s Critical Infrastructure,” available at: https://www.ncsc.gov.uk/pdfs/news/ncsc-warns-enduring-significant-threat-to-uks-critical-infrastructure.pdf.
- National Crime Agency (NCA), “NSA Cyber 2024,” available at: https://www.nationalcrimeagency.gov.uk/threats/nsa-cyber-2024.